The
second part of the tunnel, the Checkpoint NGX, a bit more things to do compared
to the Forti, but again very simple stuff.
First
create a network object to represent the internal network of the Forti , than
an interoperable device to represent the Forti gateway and add the object as
its encryption domain
Now creating
the community – the settings for the tunnel, very straight forward, choose a
name then add both the local firewall and the forti object (Just created)
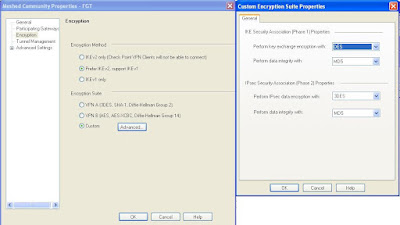
Choose
the encryption and authentication algorithms (make sure to use same settings as
the other peer)
Exclude
the IKE from the tunnel (the IKE is used
to negotiate the tunnel so it can't be inside it)
Enable
shared secret and set correct secret on the peer
And last
one for the community, set the DH groups and key life times, again must be same
as the other peer
One to
allow IKE from and to the peer and another is the actual traffic inside the
tunnel
Some
firewalls can only work with aggressive mode in case of problems suggest to try
using it instead of the main mode.
Hope this post was helpful, If it was please consider a donation:
BTC Address: 1CnyMpjd1RntRDxSus2hu2aDMyzL4Kj29N
LTC Address: LUqrKbzGihTU2GEnL3EwsuuLHCsxCJMdtR







I always add ESP and AH protocols to exclude list. And meshed VPN type is mostly built for CheckPoints - so every firewall can create a separate tunnel with other members.
ReplyDeleteGreat post, you have pointed out some excellent points, I as well believe this is a very superb website. vpn for torrenting
ReplyDeleteWhat a fantabulous post this has been. Never seen this kind of useful post. I am grateful to you and expect more number of posts like these. Thank you very much. cheap vpn
ReplyDelete